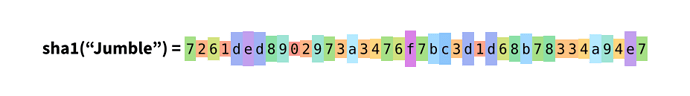Jumble is a Typst package which provides a few common hashing functions and other related methods
Currently implemented functions include:
- MD4
- MD5
- SHA1
- HMAC
- NTLM
- TOTP
Was this really something missing from Typst Universe ? Maybe not, but hey, now you can generate your TOTP codes directly in Typst ! Cool huh ?
I recommend checking out the manual to learn about the available methods and see some examples using each function
Find out more in the official repo or in Typst Universe
5 Likes
I can imagine it being useful when generating documents and presentations on cryptography or cryptographic protocols.
But I have to ask, what made you choose these algorithms instead of more modern and—by now—widely used ones (like SHA-2, SHA-3, BLAKE2b, BLAKE3)?
The original goal was just to implement TOTP (mainly for fun). This included HMAC and SHA1
But then I thought I could also implement MD4 to have NTLM (Windows passwords, which incomprehensibly bad). MD5 seemed easy and logical to add after that
I’ll probably look at SHA-2 but more recent algorithms like bcrypt might be a bit expensive for Typst
1 Like
I think this is a perfect usecase for a Typst plugin. With a plugin you can just use a Rust crate which implements the Hash functions and let it run in WASM. It will be a lot faster (and easier to implement)!
I see, that makes sense!
I’ll probably look at SHA-2 but more recent algorithms like bcrypt might be a bit expensive for Typst
The wording seems to imply some misunderstanding on the difference between SHA-2 and bcrypt. If that’s not the case, you can gladly skip this comment.
These algorithms aren’t really distinct in their age (though they weren’t invented and standardized at the same time).
Instead they were made for different purposes:
-
SHA-2 is a cryptographically secure hash function (family) that can be used for reasonably fast hashing of files, data streams, or smaller objects. Which is why it is used a lot as a building block in cryptographic protocols.
-
bcrypt on the other hand is used for one thing only: hashing passwords. People are bad at creating secure and random passwords. So if an attacker gains access to a database full of those passwords hashed using SHA-2, they can easily check what passwords the hashes belong to because the hash function is just too fast.
bcrypt tries to slow down the password cracking process a lot (and adds a salt), intending to make those attacks economically infeasible for large data dumps.
Also, as long as you don’t set the bcrypt parameters too high, it should be reasonably fast in Typst.
PS: I recommend using argon2id instead of bcrypt nowadays. It protects better against password cracking using GPUs and doesn’t cut off everything beyond the 72nd byte while hashing.
Yeah, definitely, but I’d need to learn Rust and/or how to compile to WASM 
Anyway, my goal wasn’t performance or completeness so it made sense to keep it simple (and it still runs surprisingly fast, thanks to Rust if)
1 Like
My sentence is indeed not great, sorry
What I meant is that I can probably do SHA-2 algorithms (e.g. SHA-256), but that “recent” cryptographic hashing methods (especially for passwords like bcrypt), may involve very expensive calculations (by design, obviously)
Since the initial intent was to make some basic functions that could serve some purpose (I can see some people needing md5 or wanting to use TOTP in Typst), I could still implement them although setting low costs by default
As @jbirnick said though, this would be much easier with a plugin, which is not something I plan on doing
PS: Thank you for your detailed explanation 
Jumble is now available in the Typst Universe 
1 Like
This can be used for state identifier or some generated labels to avoid duplication.
Hey this looks really promising! I’m interested in creating InChI Keys and these use SHA256 to create their Hashes. Do you think it would be possible to add SHA256 encryption to the package?
I think it’d have to be a plugin to implement SHA256 as Typst’s scripting language would probably not be efficient enough. Moreover, it would be easier to provide more hashing / encryption functions
I don’t know when I’ll come round to it. Let me know if this is urgent and I’ll try to take a look as soon as possible
Thanks for replying so quickly! No it’s not urgent, but please do let me know if you get around to doing it! I myself sadly just don’t have the cryptography experience to do it
1 Like